1. AD RMS Overview
AD RMS is information-protection or information
rights management (IRM) technology that provides organizations with the
means to better safeguard sensitive information. It does this by
enforcing policy through applying persistent protection to the e-mail
or document, allowing the publishers of confidential e-mail messages
and documents to control who can view their content. This is done using
public key technology using XrML (Extensible Rights Markup Language)–based certificates.
Note:
AD
RMS is not a replacement for your X.509 PKI implementation, even though
AD RMS is based on public/private key technology; the two are
complementary, and provide different solutions for different problems.
In the same vein, deploying RMS does not require you to implement a PKI
certificate authority (CA).
Persistent content
protection is the fundamental distinguishing feature of AD RMS that
differentiates it from other encryption technologies such as S/MIME or PGP.
A user who has opened an S/MIME encrypted e-mail message using his keys
has complete control over the message while he has it opened; he can
forward it, cut/copy/paste the contents, print the message, and so on.
The persistent content protection provided by AD RMS means that as well
as when the material is unopened, the rights the user has over the
content are also explicitly defined and enforced while the user has the
e-mail or document open. Those rights also persist with the message
whether it is in an Exchange Server 2010 mailbox, in a PST file, or
wherever else it may exist. The most important concept is that rights
are enforced while the message is opened, meaning that the recipient
cannot forward, print, cut, copy, or paste the message unless the
explicit rights to perform these actions have been granted.
Users present valid Active Directory credentials to the AD RMS server and are then granted a Rights
Account Certificate (RAC—their RMS credentials). The AD RMS client on
the user's computer also generates a certificate for the client
computer, and the user's RAC is encrypted with this machine
certificate. If the user moves to a different client computer, another
instance of her RAC is obtained from the RMS server, encrypted for the
new client computer.
In addition to the RAC, a user is also issued a Client
Licensor Certificate (CLC). The CLC enables the user to encrypt
(protect) content without contacting the AD RMS server, to facilitate
working offline; offline publishing is the default behavior for the RMS
client.
When an RMS-protected e-mail
is received by a user, that user is provided a use license issued by
the RMS server which grants them rights for that e-mail. Use licenses
are encrypted with the user's RAC and bound to a specific client
computer with that client computer's machine certificate, similar to
the user's RAC. RMS-protected content can be encrypted to a single user
or to distribution groups.
The various certificates
issued to users can be viewed in the user's profile, including RACs,
CLCs, use licenses, and the machine certificate. Note that if the user
only accesses RMS-protected e-mail via Outlook Web App, these
certificates won't be stored in his local user profile and instead will
be stored on the Exchange Server 2010 Client Access server. In Windows
7, these certificates are located at %userprofile%\AppData\Local\Microsoft\DRM.
The components of an AD RMS implementation are outlined in the following list; all of these components are required except for AD RMS templates. Templates are not required for the base functionality, but may be required to use some of the features of AD RMS integration with Exchange Server 2010.
Active Directory AD
RMS uses Active Directory to authenticate and authorize users as well
as to look up group memberships for content protected to groups. This
is done by referencing the user or group's SMTP addresses, including
proxy addresses. To reduce the number of Active Directory lookups
performed by AD RMS, group memberships are cached in SQL.
AD RMS cluster An AD RMS cluster is composed of one or more AD RMS servers. The AD RMS server is a Windows Server 2008 SP2 or Windows Server 2008 R2 computer on which the AD RMS role has been installed. This role has a Web service that handles the XrML-based licensing of rights-protected information,
enrollment of servers and users, certification of trusted entities such
as users and computers, and administration functions. The AD RMS server
role requires the Microsoft Message Queuing service, IIS, and ASP.NET; these required services are installed automatically when the AD RMS role is installed.
Database server AD RMS uses a SQL
Server database—either SQL Server 2000 SP4 and higher, SQL Server 2005
SP3 and higher, or SQL Server 2008 SP1 and higher. A single-server AD
RMS cluster can use the Windows
Internal Database feature of Windows Server 2008 or Windows Server 2008
R2 for testing purposes, but is not recommended for use in a production
deployment.
AD RMS client
The AD RMS client software is an integrated component of Windows Vista,
Windows 7, Windows Server 2008, and Windows Server 2008 R2. For Windows
XP SP2, Windows Server 2003, and Windows Server 2003 R2, the SAD RMS
client is a separate download and install.
RMS-aware applications Applications must be AD RMS–aware to be able to use its capabilities.
An application being AD RMS–aware means that:
It relies on the AD RMS client for encryption/decryption.
It enforces the rights defined in the publishing license for the document or e-mail.
It can directly or indirectly call the RMS Web services.
It is certified by Microsoft via an application manifest signing process.
From a client computer perspective, Office 2003 Professional and higher or Office
2007 Professional Plus and higher are supported out of the box for
protecting content. Office 2003 Standard and Office 2007 Professional
can access RMS-protected content only; they cannot access RMS-protect
content. Outlook e-mail messages and Microsoft Word, Microsoft PowerPoint, and Microsoft Excel files can all be RMS-protected, as can XML
Paper Specification (XPS)–based documents. RMS functionality can be
extended with third-party products into other applications and file
formats, such as PDF, CAD/CAM file formats, and BlackBerry Enterprise Server. Exchange Server 2010 is also AD RMS–aware; in many ways, from the perspective of the AD RMS cluster, Exchange Server 2010 is simply another client.
AD RMS templates AD
RMS templates provide a predefined set of user/group and rights
combinations that facilitate the consistent application of RMS
protection to content. These templates are defined on the AD RMS server and stored in the SQL database used by AD RMS. The AD
RMS templates are also exported in XML files to a location configured
on the AD RMS cluster for use by AD RMS clients. These XML files are
used by clients to view and select the AD RMS template to apply to the
content. To be usable for end users, the AD RMS template XML files must
be made available to them.
Note:
AD RMS templates
are best used sparingly to keep the AD RMS deployment manageable and so
that the list of options presented to end users is as short as
possible. As an example, an organization of more than 250,000 users
uses AD RMS with fewer than five templates for the entire organization.
1.1. AD RMS Templates
Although AD RMS templates (also known as distributed rights policy templates)
are optional for end users who are applying IRM permissions to
documents or e-mail messages manually, they are required for Exchange
Server 2010 to apply IRM protection via either transport rules or
Outlook Protection rules.
Exchange Server 2010
uses AD RMS templates when applying IRM to e-mail messages. If no
templates have been defined by the AD RMS administrator, the built-in Do
Not Forward functionality can be used. Do Not Forward is a client-side
template that grants edit, view, reply, and reply all permissions to
recipients of an e-mail message. This client-side template is a
built-in function of the AD RMS client, and is available to Outlook and
Exchange Server 2010 as a selectable template for Exchange Server 2010
transport rules and Outlook Protection rules, independent of whether AD
RMS distributed rights policy templates have been created.
The components of an AD RMS template are as follows:
Template Identification The template
identification defines the language or languages of the template, the
template name (displayed in the Permissions menu in Outlook or Outlook
Web App), and a template description (displayed to the recipient of the
IRM-protected e-mail). The template name and description are configured
separately for each language supported in the template.
User Rights
The user rights define what users or groups are granted permissions by
this template and what permissions those users or groups receive. You
can have multiple users or groups specified, with each entry receiving
different permissions. For example, All Employees could be granted Full
Control, whereas Sub-Contractors may be granted only View permissions.
Expiration Policy
The expiration policy dictates how long content is accessible by
recipients. For example, the policy can be defined to not allow access
after 31 December 2010, or to not allow access after 30 days. By
default, the author of the content always has access, even after the
content has expired.
Extended Policy
The extended policy dictates whether users can view content using a Web
browser add-on, or whether clients need to obtain a new use license
(contact the AD
RMS cluster) every time content is consumed. Caution should be used
when configuring a template to require a new use license every time
content is consumed; this will increase network traffic and make the
content unavailable to offline users. By default, use licenses are
cached with the IRM-protected content, so the client only needs to
contact the AD RMS cluster the first time content is consumed. Note
that requiring a new use license every time content is consumed means
that Exchange Server 2010 will be unable to pre-fetch use licenses for
e-mail protected with that template.
Revocation Policy
Using revocation policies provides you the ability to revoke content
protected using this template. This option is not typically used
because it requires additional administrative overhead and requires
that the published revocation list be always available to all clients
when they attempt to obtain a use license for content protected with
this template. If the revocation list is unavailable, clients will be
unable to access content protected with this template, although users
(content owners) by default always have access to content they have
created.
1.1.1. Creating Distributed Rights Policy Templates in AD RMS
For AD RMS clients—including Exchange Server 2010—to use AD RMS templates, the XML files associated with those templates must be made available to the clients. This is accomplished with the following steps:
Log
on to a server in the AD RMS cluster with an Active Directory account
that is a member of the local AD RMS Enterprise Administrators group on
the server.
Start the Active Directory Rights Management Services management console from Administrative Tools.
In
the Active Directory Rights Management Services management console,
expand the AD RMS cluster in the left-hand pane and select Rights Policy Templates. In the Results pane, click the Change Distributed Rights Policy Templates File Location link and then select the Enable Export check box as shown in Figure 1. Enter the UNC path for the file share to export the template files to and then click OK.
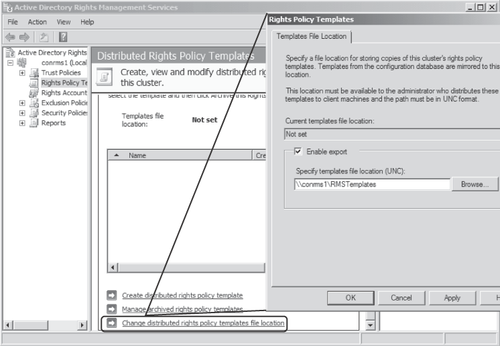
Note:
The
file location specified should already exist, and the RMS service
account needs to have write permission to the file share. In addition,
clients accessing the template files from this location need to have at
least read permission to the file share.
When the distribution point for the template XML files has been configured, you create distributed rights policy templates using the Create Distributed Rights Policy Template Wizard in the AD RMS management console as shown in the following steps:
Log
on to a server in the AD RMS cluster with an Active Directory account
that is a member of the local AD RMS Enterprise Administrators group on
the server.
Start the Active Directory Rights Management Services management console from Administrative Tools.
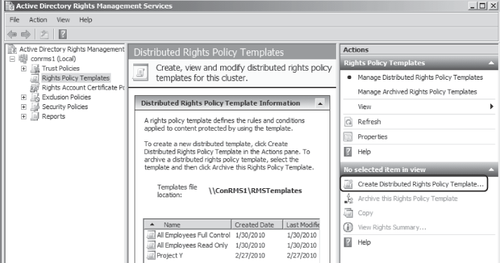
In
the Active Directory Rights Management Services management console,
expand the AD RMS cluster in the left-hand pane and select Rights Policy Templates. In the Actions pane, click Create Distributed Rights Policy Template as shown in Figure 2 to start the Template Creation Wizard.
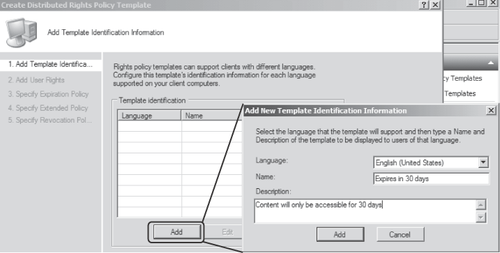
On the Add Template Identification Information page of the wizard, shown in Figure 3,
click Add. Select the language for the template, enter an appropriate
name and description, and then click Add to apply the settings and
return to the wizard. Click Next.
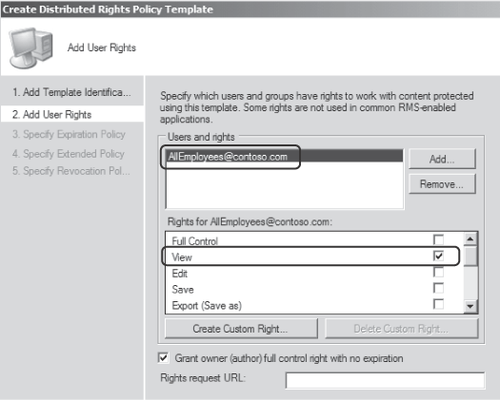
On
the Add User Rights page of the wizard, click Add to add the
appropriate user or group to the template. Back on the Add User Rights
page, highlight the added entry and select the appropriate rights for
the user or group as shown in Figure 4. Click Next.
On the Specify Expiration Policy page, configure the content expiration settings as appropriate and click Next.
On the Specify Extended Policy page of the wizard, click Next.
Click Finish on the Specify Revocation Policy page to complete the wizard and create the template.